While Microsoft is preparing the early 2023 Microsoft Intune Endpoint Privilege Management solution public preview, I will kickstart the waiting time with my personal ramblings regarding Endpoint Privilege Management and managing Administrative Privileges.
With Microsoft Endpoint Privilege Management, you will no longer need to give users Local Administrative Privileges. Instead, your users can have Standard Privileges and be Dynamically Elevated to have privilege required for specific administrative tasks, improving productivity while enhancing security posture.
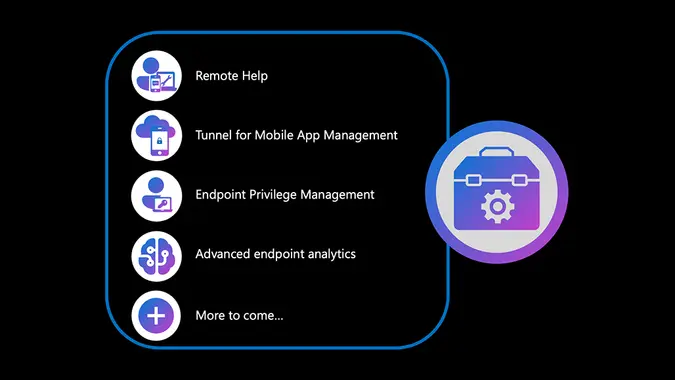
Microsoft Endpoint Privilege Management (EPM) is part of the Advanced Endpoint Management product family, expected to be generally available around March 2023, and will include Remote Help, Microsoft Tunnel for Mobile Application Management, Endpoint Privilege Management, as well as Advanced Endpoint Analytics, App patching and packaging, and more.
References:
- Introducing advanced Endpoint analytics with Microsoft Intune Suite
- Microsoft Advanced Endpoint Management
- Reduce your overall TCO with a new Microsoft Intune plan
- The Microsoft Intune Suite fuels cyber safety and IT efficiency
- What are advanced Endpoint analytics
For decades, users have had Administrative Privileges on their own computer, they have been allowed to manage and install software on their own device without any form of audit, and over the years we have seen incidents happening all over the globe, and many of these was often the result of users either clicking malicious links or installing compromised software. Today the complexity of these attacks has tripled and within any organization, removing Administrative Privileges for users on corporate computers has become a central task.
Unfortunately, organizations often find themselves in a situation, where history, traditions for manual software management, profile or type of an organization, poor or missing application lifecycle management, often force them to postpone the task, in some cases an old and outdated application might require to be run as local administrator, is the sole reason for the task to be postponed.
Within any organization and IT departments, we experience a strong desire to remove Administrative Privileges for end users on their own devices. Privileges usually are split into two levels of hierarchy: Standard User and Privileged User (Local Administrator), and in most cases, it makes perfectly sense, only allowing Standard User Privileges, however most organization will most likely have a subset of users who will need Administrative Privileges to remain productive.
Complexity and dilemmas
The complexity and dilemma arise, when a strong desire to remove Administrative Privileges for end users, often conflicts with an equal strong desire to give users the ability to re-gain temporary Administrative Privileges on their personal computer.
Vendors often overplaying the privileged access threat landscape, with a higher risk of enabling cyberattacks and severe consequences - however, Endpoint Privilege Management should not be the only solution when architecting to defend against exploitation scenarios to resist advanced malware attacks.
It is very important for organizations to fully understand the challenges, issues, and functionality an organization want to achieve, does an organization have old and outdated application which is requiring to be run as local administrator, have a tradition for users updating and installing third-party software or does some users have to do tasks, require them to elevate to gain administrative privileges to remain productive.
The solution might lay in implementing Endpoint Privilege Management (EPM); however, every organization must measure their internal maturity, and ensure to utilize modern and up-to-date operating systems, implement modern security measure, on Windows these security measure would require enabling:
- Windows Hello for Business
- Microsoft Defender Credential Guard
- Microsoft Defender Application Guard
- Microsoft Defender Application Control
- Microsoft Defender Attack Surface Reduction
These security measure will help protect against common attack vectors, like Pass the Hash Attack (PtH), unintentionally running maliciously or untrusted software, protect against programs or processes creating maliciously sub-processes - even if the user is running with Administrative Privileges on their own computer. It is important to understand security measures mentioned, are only part of the overall solution, and strong and recommended platform security settings and thorough update policies must be implemented in parallel.
The right purpose and the right solution
The proper solution will most often be, to remove Local Administrative Privileges - in a domain environment, removing Local Administrative Privileges is a must do task, due to the way domain joined devices, are interconnected, and might share user accounts, access tokens etc.
The purpose of an Endpoint Privilege Management (EPM) solution should always be clearly stated, and Endpoint Privilege Management (EPM) should be the process of allowing employees enough access to remain productive in their roles, without giving them Administrative Privileges over their IT system.
In short, with Endpoint Privilege Management (EPM) employees are not granted permissions for more than what is required of their role - in cybersecurity, this is defined as the “principle of least privilege”.
Benefits of using Endpoint Privilege Management (EPM):
- Permit to remove Administrator Privileges from users.
- Permit to assign Privileges to applications and not users.
- Provides centralized management.
For organizations to be able to remove Local Administrative Privileges with no, or minimal impact, a clear insight and understanding of the infrastructure requirements, software and application portfolio is essential. Furthermore, organizations must have the appropriate insight to successfully configure applicable Endpoint Privilege Management (EPM) policies allowing trusted applications to execute with the lowest possible privileges.
While moving away from traditionally domain joined devices, and focusing on modern devices, these devices does not have a traditional connectivity to “everything” and is decoupled from “everything”. Cloud-only, or Azure-AD-joined devices, support the journey towards a cloud-only environment, allowing organizations to manage corporate-owned devices by joining the device directly to their Azure AD.
Azure AD joined devices are signed in to, using an Organizational Account (Azure AD account), and access to resources can be controlled based on the Azure AD account state, device compliance while Conditional Access policies will apply, and due to the “stand-alone device state”, the device will be more resilient than traditional domain joined devices, and at the same time protecting the user credentials without sacrificing user experience.
Whatever setup an organization have, Endpoint Privilege Management (EPM) must not be the tool to make every device, user role and user tasks behave evenly, it should be a tool to enhance usability in the scenarios where the user cannot do their job when removing Administrative Privileges from the end user device.
In the scenarios where a user’s job role require the user to have Administrative Privileges on their own device, other security measures and configuration should be in place allowing, e.g., consultants and engineers to keep Administrative Privileges on their own computer, however this might come with some limitations, e.g., device should be cloud-only, and users might not be allowed access to internal resources, remote access using VPN or similar, and will be directed to access resources using Remote Desktop Services, Windows 365 or comparable.
Closing thoughts
Organizations with no clear view of the requirements, others than user should not be granted Local Administrative Privileges, or if no final decision or proposal is made towards any product, and consequently no clear functional requirements is made - I propose all devices will be provisioned with Standard Privileges. If then, users with special user roles, or requirement to keep Local Administrative Privileges on their own device to stay productive, a special software package should be crafted, for these users to request, permitting Permanent Local Administrative Privileges on their own device.
This is achievable, if you ensure to utilize modern and up-to-date operating systems, implement modern security measure, on Windows these security measure would require enabling:
- Windows Hello for Business
- Microsoft Defender Credential Guard
- Microsoft Defender Application Guard
- Microsoft Defender Application Control
- Microsoft Defender Attach Surface Reduction
These security measure will help protect against common attack vectors, like Pass the Hash Attack (PtH), unintentionally running maliciously or untrusted software, protect against programs or processes creating maliciously sub-processes - even if the user is running with Administrative Privileges on their own computer.
It is important to understand, security measures mentioned, are only part of the overall solution, and strong and recommended platform security settings and thorough update policies must be implemented in parallel.
Happy exploring.
–Jesper